AI Agents Are Taking Over: How Autonomous AI is Reshaping Work in 2025
The future of work isn’t coming—it’s already here, and it’s powered by AI agents that…
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis.
Discover a unified cybersecurity solution covering asset management, identity and access management, user access review, network security, and data protection.
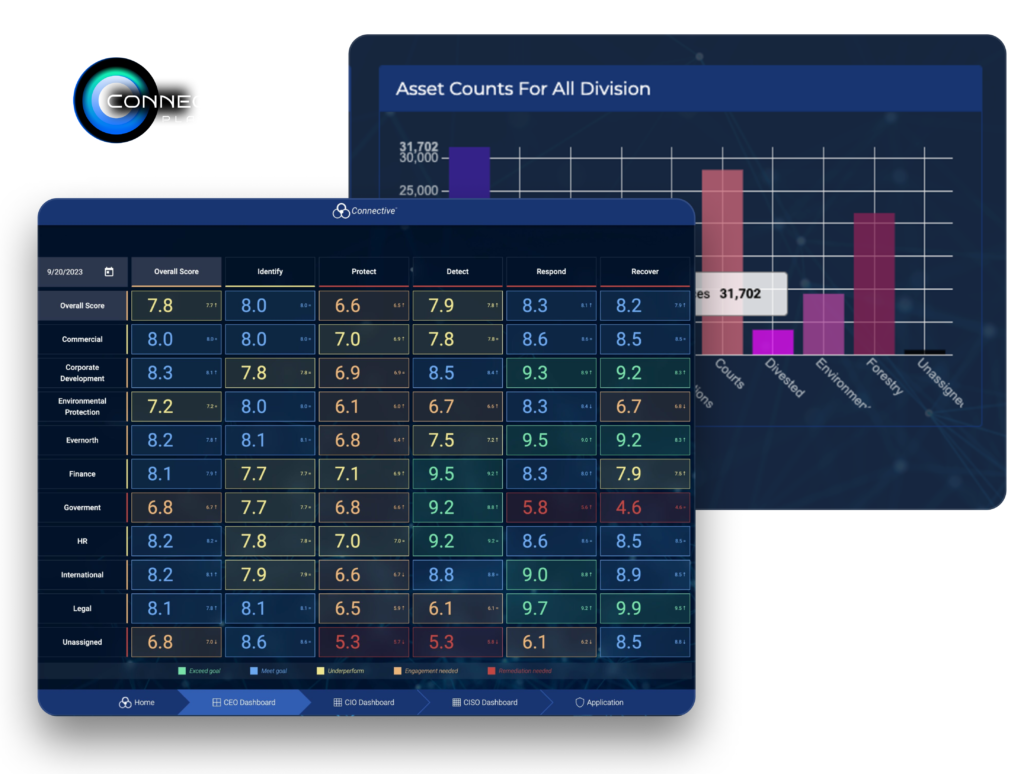
Customizable, audit-ready dashboard offering real-time insights into your organization's cybersecurity posture.
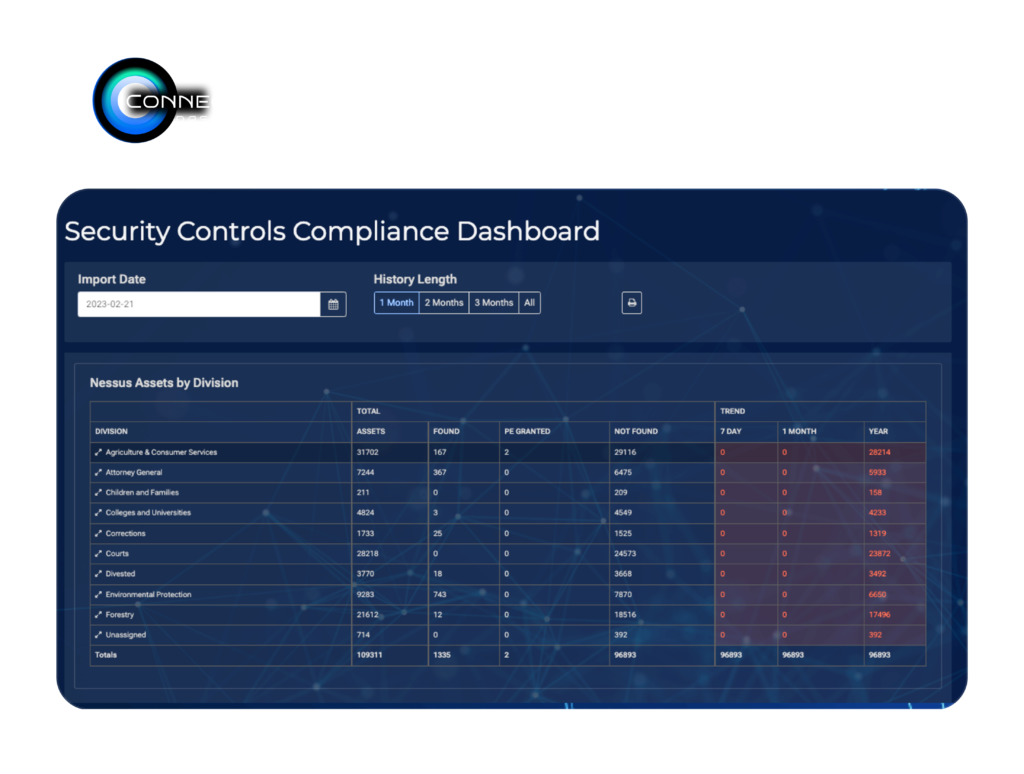
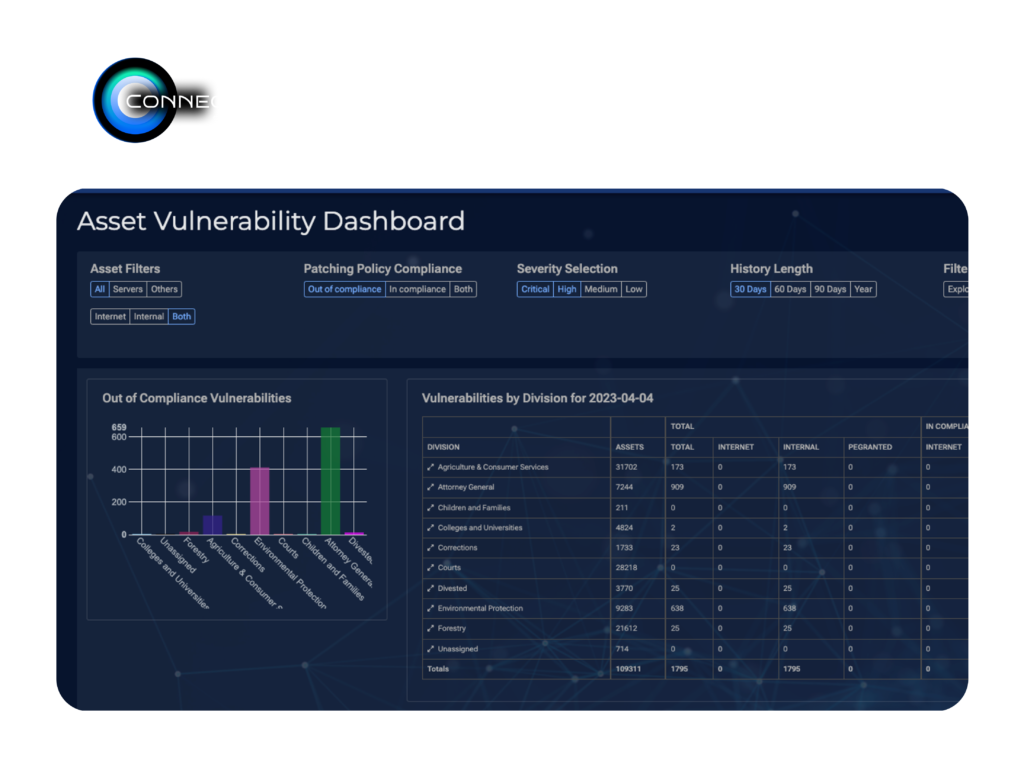
Advanced threat detection and network security with continuous monitoring and automated defenses.
Comprehensive platform designed to secure, manage, and streamline digital identities across your organization’s network.

Offers a powerful and comprehensive platform designed to help organizations monitor access rights across their digital landscape, ensuring all user access is appropriate, compliant, and aligned with organizational policies, reducing the risk of security breaches and non-compliance.

Let our experts build a cybersecurity strategy to safeguard your business’ information systems and data.
Technology focused Advisory services for CEOs and Boards focused on profitable growth, strategic execution, people development, and business diversification.
Advisory services focusing on emerging technologies, digital transformation, and maintaining cybersecurity.
Business-IT integration services to navigate and stay ahead of the evolving technology landscape.
Expert IT guidance for organizations transitioning to or expanding in the cloud, ensuring best practices and cybersecurity readiness.





C3 is driven by the need to look at cybersecurity as primarily a business problem, not a technology problem.
Led by cybersecurity expert Rodrigo Loureiro, C3 provides advanced security solutions tailored to your business needs. We put diverse cybersecurity tools into a single, user-friendly platform.
Our Connective Platform fits perfectly with your current tech, giving you accurate, ready-to-use data. With C3, your information is always available, accurate, and easy to use.
The future of work isn’t coming—it’s already here, and it’s powered by AI agents that…
Here’s a sobering reality: Companies spent $180 billion on cybersecurity tools in 2023, yet breaches…
Board meetings have changed. Gone are the days of technical jargon and security metrics that…
The Cyber Connective Platform is a software solution provided by C3 – Cyber Connective Corporation that integrates cyber security risk management, cyber security operations, and regulatory compliance, creating a standardized model of all cyber security data for LLM training.
The platform is designed for businesses and organizations needing to manage cyber security risks and ensure regulatory compliance.
The purpose of the Cyber Connective Platform is to provide a solution for cyber security risk management, unifying cyber security risk management with cyber security operations and regulatory compliance. It creates a normalized and standardized model of all cyber security posture data for LLM training.
C3 implements appropriate measures to protect data security and confidentiality. Users are required to comply with data protection laws and avoid using the platform for unlawful data processing.
The annual cost is based on the number of digital assets and digital identities.
Users are granted a non-exclusive, non-transferable, revocable license for internal business purposes, subject to the platform’s terms. Resale, distribution, public performance, leasing, or commercial exploitation is not permitted.

The call will be held personally by the founder and CEO of C3
Leveraging unique expertise and global experience from leading and experienced executives.
Copyright © 2024 Cyber Connective Corporation