Discover a unified Connective Platform covering asset management, identity and access management, user access review, network security, and data protection.
Track and manage all digital assets with real-time visibility across your entire organization.
Review and audit user permissions to ensure your organization remains compliant and secure.
Continuously monitor your network for potential threats and vulnerabilities, preventing breaches before they happen.
Secure and control who can access your systems and data with advanced user access management.
Safeguard critical business data with comprehensive protection across all digital assets.
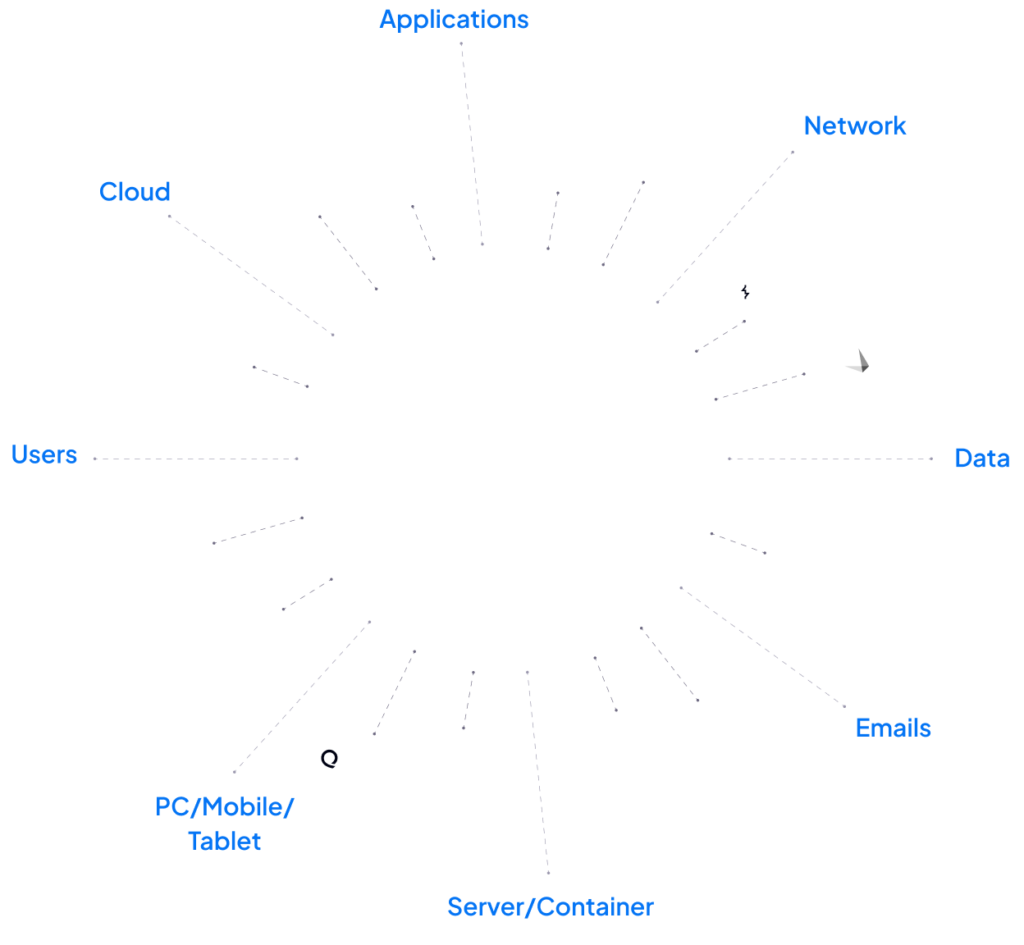
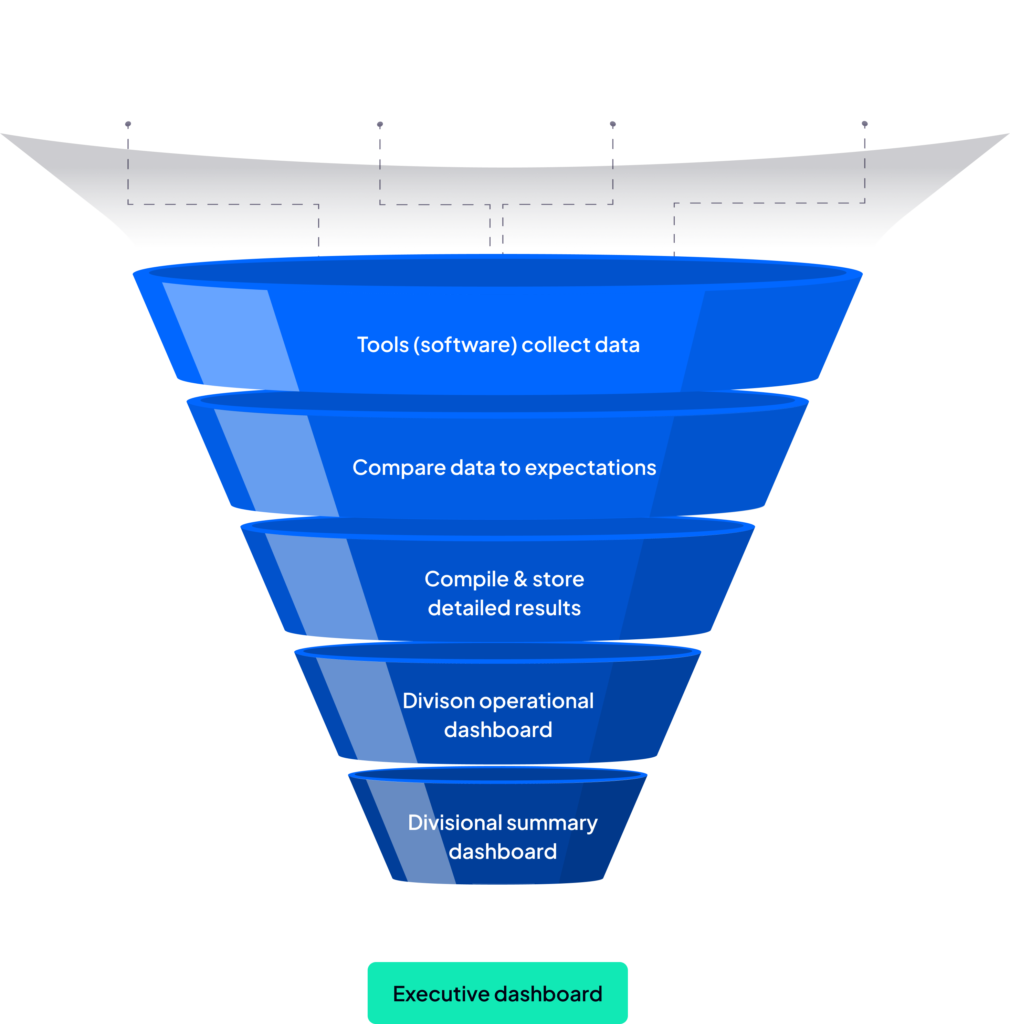
The C3 platform connects with all your existing cybersecurity tools, combining data from every asset, user, and security system in a single, auditable view. This connectivity streamlines your operations, eliminates manual processes, and ensures full oversight of your cybersecurity landscape.
C3 consolidates existing products into a single, normalized view, reducing manual effort. Executives, shareholders, and business leaders can easily access the data they need, enabling faster decision-making and more effective risk management
Eliminate manual processes, saving time and resources.
Streamline communication between business leaders and security teams.
Consolidate asset views for multiple teams across the organization.
C3 is designed to help CISOs and other security leaders deliver clear, confident updates on the organization’s security posture to boards and executives. The platform aligns cybersecurity risks, resources, and projects with your overall business strategy, empowering decision-makers with real-time data.




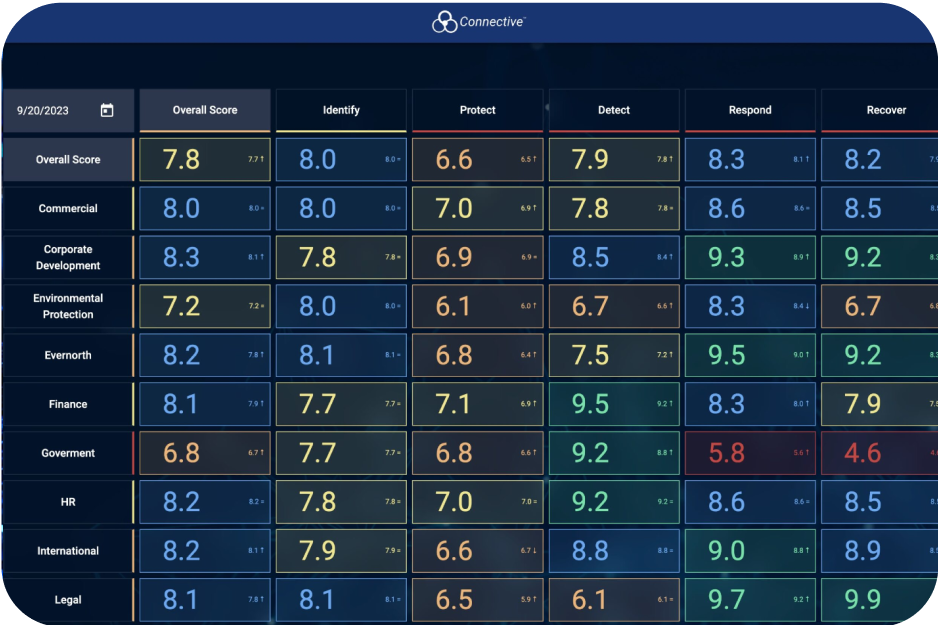
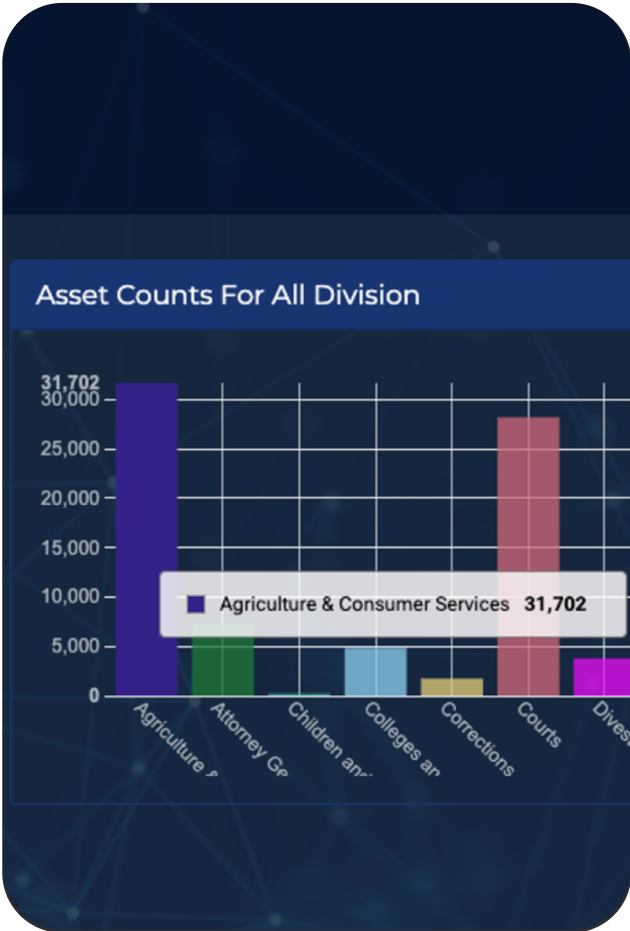
Get full visibility into your organization’s security status through customizable dashboards designed for various roles. With real-time reporting and data visualization, you can ensure alignment between your security efforts and business goals, while easily presenting clear updates to stakeholders.
The Cyber Shield is a core part of the Cyber Connective Platform, offering advanced protection for enterprises worldwide. It delivers full asset management, identity and access control, network security, and data protection, all within a single platform.
With Cyber Shield, you gain a clear, auditable view of your entire cybersecurity program through an easy-to-use dashboard. This platform also ensures seamless interoperability between various cybersecurity tools, normalizing data into a unified view.




The С3 platform supports compliance with key frameworks like NIST-CSF, and enables risk-based scoring and prioritization for clear, actionable evaluations. Our reporting tools provide detailed insights into risk mitigation efforts, helping your organization stay compliant and minimize risks efficiently.

A large college in Peru with multiple campuses, serving over 120k students, 15k staff, and managing around 1500 sensitive assets both on-premise and in the cloud.
Incorrect asset mapping
Lack of visibility into the application stack
Disparate cybersecurity tools (Tenable IO, Tenable on-prem, Tenable WAS)
Deployed the C3 Connective Platform, which consolidated tools and enabled full visibility into all assets.
Integrated data from all tools, ensuring interoperability and historical data access.
Created a unified application stack that correlates assets, network, and access data with the business application stack, providing improved governance and control.

The call will be held personally by the founder and CEO of C3
Leveraging unique expertise and global experience from leading and experienced executives.
Copyright © 2024 Cyber Connective Corporation